Let’s Encrypt is cool. It is more than enough for most of your SSL needs. Not only because it’s free, it can also automatically renew the SSL certificate for you (so theoretically you don’t need to do anything). You can always use Let’s Encrypt for your Nginx, Apache2, or anything else. One thing that you need to be aware of is that by default, it won’t reload / restart your web server after successful renewal. Then eventually, you will realize that your site is running under an expired SSL certificate while you see on the server that your certificate is still valid.
This problem isn’t a Let’s Encrypt bug nor the webserver’s. What you really need to do is just simply reloading / restarting your web server so it will load the newly renewed certificate. Otherwise, your web server will keep serving with the old expired certificate.
For Nginx, you can always do /etc/init.d/nginx reload, but you can automate it after successful Let’s encrypt renewal by using post_hook renewal parameter in your Let’s Encrypt domain renewal config. This way you can configure the post_hook configuration for each domain. Edit the file located at /etc/letsencrypt/renewal/yourdomain.com.conf and append post_hook parameter as below:
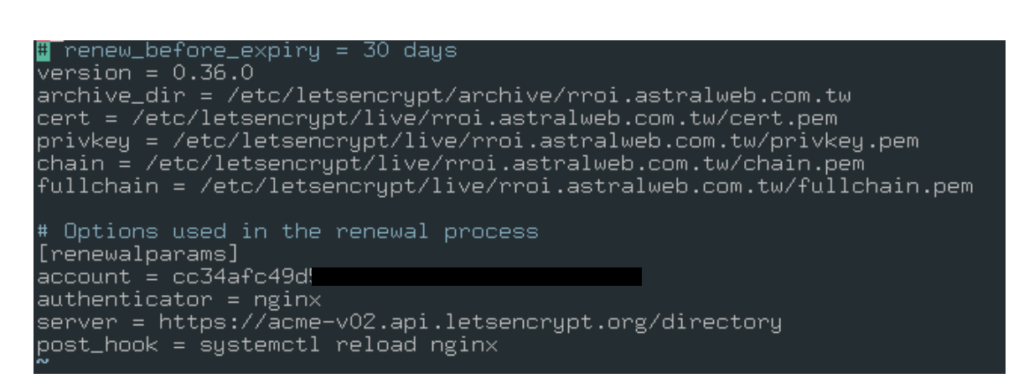
The second method, you can setup the renewal hook action for all domain by writing a simple script under /etc/letsencrypt/renewal-hooks/deploy/ and let’s name it with 01-reload-nginx. The full path is /etc/letsencrypt/renewal-hooks/deploy/01-reload-nginx.
Put this inside the file:
#! /bin/sh
set -e
/etc/init.d/nginx configtest
/etc/init.d/nginx reload
Then, save, and run the following command to make it executable:
chmod a+x /etc/letsencrypt/renewal-hooks/deploy/01-reload-nginx
Voila!


