The main purpose of Magento is to allow merchants and clients to perform purchasing-related operations, but Magento also provides mechanisms for allowing external applications to communicate with it.
SOAP
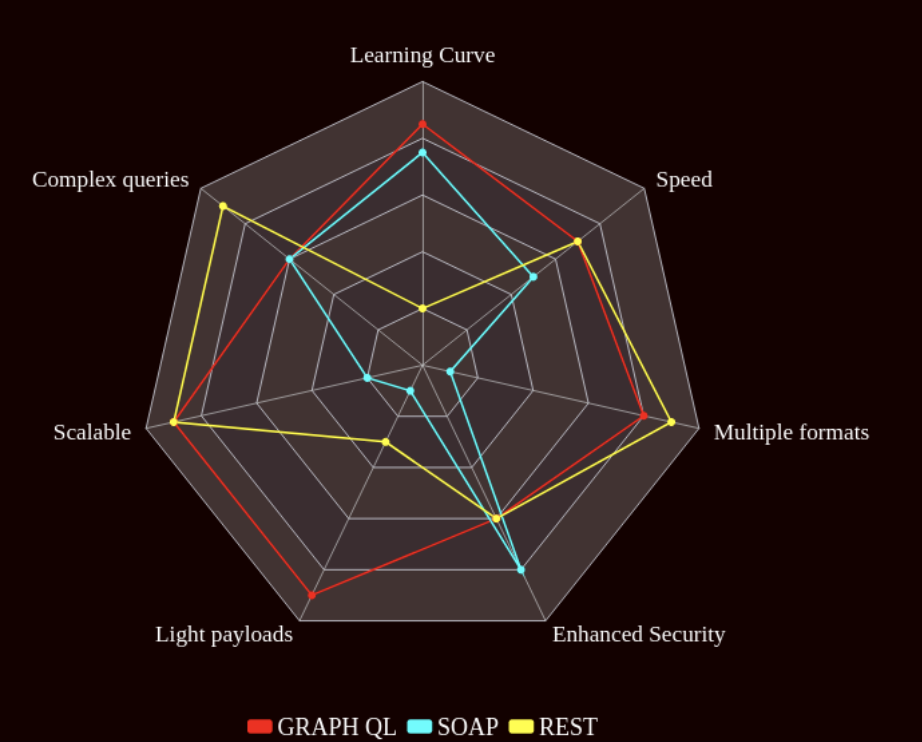
This protocol is the least popular among all the protocols provided by Magento due to its complex learning curve. It is also the least flexible, because it only works with XML; not ideal for speed performance because the payload sizes tend to be big.
However, the lack of flexibility ensures great security and tends to enforce a clear business flow when interacting with the API.
When to use it?
- The project requires a very strict request logic.
- Performance speed is not critical.
- There is plenty of time for studying the protocol.
- No need to scale in the future.
REST
At the moment of writing this article this is the most popular API protocol; so it is the most documented API, converting it into the entry point of many new developers into API development.
Its messaging format is very flexible, allowing many formats such as JSON, XML, objects, Simple Text, etc.
Since it is the most popular API protocol, it is cache friendly in almost all web browsers and HTTP protocols; however, storing huge amounts of unnecessary data is the biggest flaw.
When to use it?
- The project requires a simple API protocol that follows standard conventions.
- Performance speed is not critical.
- Very little time left in the project.
- More suitable for complex database querying.
- Scalability is required in the future.
Graph QL
The newest of the API provided by Magento, improves speed performance by only returning the info required; however, the learning curve is very steep; also, not suitable for complex querying, because it will reduce its original performance speed for handling nested queries.
When to use it?
- Performance speed is critical.
- No need for performing nested queries.
- Need to update the project with the newest GraphQL technology.
- There is plenty of time for learning/studying.
- Scalability is required in the future.
According to the documentation, Magento supports SOAP, REST, and GraphQL protocols, allowing almost any external system to communicate with its database/entities; however, when developing a new Magento API, the developer must understand how to choose the correct protocol for the right situation; at the end this will help a project to run smoothly.